PPTP vs. L2TP: What’s the difference?
The Point-to-Point Tunneling Protocol (PPTP) and Layer 2 Tunneling Protocol (L2TP) are both virtual private network (VPN) tunneling protocols, but they function very differently. All VPNs direct internet traffic through an encrypted tunnel, though the protocols they use vary.
PPTP is an older protocol that saw wide use in the late 1990s. L2TP comes from the same era, and though better in terms of security, both protocols are lacking when compared to more modern options. That said, the two protocols are worth learning about as parts of cybersecurity history.
What is PPTP?
PPTP is one of the earliest methods for building a VPN. It was often used to enable remote employees to securely access corporate resources over dial‑up and, later on, broadband internet.
At a high level, PPTP encapsulates Point‑to‑Point Protocol (PPP) frames into IP packets and sends them through the internet. The process is handled by two channels: a control channel and a data channel using Generic Routing Encapsulation (GRE). Once both channels are set up, traffic flows between the user and a private network as if they were directly connected.
While it is technically a VPN protocol, the original release of PPTP did not provide any encryption. This was eventually added in implementations that incorporated Microsoft Point‑to‑Point Encryption (MPPE), but even these security measures are now considered outdated and insecure.
In contrast, modern VPN protocols incorporate encryption as a default feature. Given that protocols like Lightway and WireGuard are both faster and more secure, there’s really no reason for most users to opt for PPTP.
How PPTP works
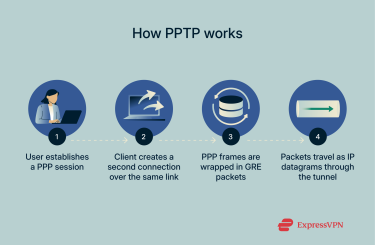
When a user initiates a connection with a PPTP VPN, their device first establishes a PPP session with an access server, such as your internet service provider (ISP). Once authenticated, the client sets up a second connection to the PPTP server on the end user’s network.
That second session is managed using Transmission Control Protocol (TCP) port 1723. The PPP frames are then wrapped into GRE packets, which are sent out as IP datagrams. This process creates a tunnel through which data can flow.
PPTP supports voluntary and compulsory tunneling modes. In voluntary tunneling, the client initiates the tunnel after obtaining an internet connection. Compulsory tunneling is started by the server or network and can force all of the network's traffic through the VPN.
Because PPTP uses the GRE tunneling protocol for data, many firewalls block it by default. To get around this, an exception must be written into the firewall. PPTP was also designed around dial‑up access and often struggles when paired with Network Address Translation (NAT), the technology that provides most networks with service today.
Some implementations of PPTP offered optional encryption using MPPE, but by default, PPTP does little to prevent data from being intercepted and read.
When PPTP was popular
In the late 1990s and early 2000s, PPTP was a popular remote‑access protocol. It was simple to set up and efficient with resources, which was useful given the hardware of the time. The protocol was built into Windows 95 and subsequent versions, and its client was included with many operating systems from that era.
But over time, researchers uncovered multiple vulnerabilities in PPTP’s challenge‑handshake authentication. MPPE was also found to have flaws, meaning PPTP couldn’t be trusted to provide secure encryption. By the mid‑2000s, experts determined that the protocol was not sufficiently secure.
These issues, coupled with the rise of more secure alternatives such as L2TP/IPsec and OpenVPN, caused a gradual but decisive shift away from PPTP. Aside from niche use on legacy hardware, PPTP is essentially obsolete.
Advantages of PPTP
Although PPTP is outdated now, it was once quite popular, in large part due to its simplicity.
Native support in legacy systems
PPTP is integrated into many older versions of Windows, macOS, Linux, and even legacy mobile platforms. You don’t need additional software to create a VPN tunnel; instead, you simply enter a server address, username, and password. This native support and simple design make it accessible for non‑technical users and facilitate stable VPN performance.
Fast setup and configuration
Because it requires minimal parameters and no certificates, setting up a VPN connection with PPTP takes only a few steps. The lack of complex authentication mechanisms means extensive technical experience is not needed to set up a remote connection.
High-speed connections
Weak encryption (or a complete lack of it) is a security concern, but it also means that PPTP has little overhead. As a result, it can often perform better than more secure protocols. Overall, PPTP can provide a very fast VPN connection. This was especially appealing during the era of slow dial-up or broadband connections.
Disadvantages of PPTP
PPTP’s advantages come at a significant cost in terms of security. It has other issues as well, which ultimately led to the protocol falling out of use.
Outdated security protocols
PPTP relies on Microsoft Challenge-Handshake Authentication Protocol version 1 and version 2 (MS-CHAP v1/v2) for authentication and MPPE using Rivest Cipher 4 (RC4) for encryption. Studies from the late 1990s identified serious weaknesses in both CHAP and MPPE, making PPTP insecure compared to virtually all modern VPN data protection protocols.
Easily blocked by firewalls
PPTP uses the GRE protocol for data traffic. Many firewalls and NAT devices block GRE by default because it lacks port numbers. PPTP is either unable to get past or struggles with strict firewalls. Routers often need to have special pass-through settings configured to let the connection through.
No encryption by default
The PPTP standard does not include complex encryption or authentication. This leaves it to the user to set up encryption. The problem is that MPPE, the standard method for encrypting PPTP tunnels, is itself highly vulnerable to modern attacks. It’s limited to 128 bits, while modern alternatives support 256-bit encryption, the new standard in many settings.
What is L2TP?
L2TP is a tunneling protocol designed to transport traffic across public networks. L2TP encapsulates data at the data‑link layer (Layer 2 in the OSI model) and can tunnel different network protocols, making it useful for bridging remote networks.
Although generally more secure than PPTP, L2TP is still considered outdated. Given the existence of better, more modern protocols, there’s little reason to use it.
How L2TP works
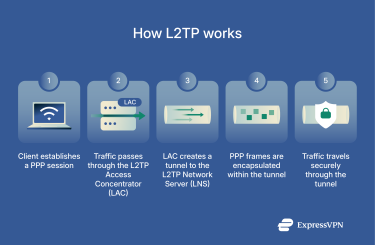
When a client connects using L2TP, the device first creates a PPP session. It then passes traffic from the session to the L2TP Access Concentrator (LAC).
The LAC assigns an IP address to the client and initiates a tunnel to the L2TP Network Server (LNS). Once the tunnel is established, PPP frames are encapsulated within L2TP packets and forwarded across the network. Control packets maintain the tunnel, and data packets carry the encapsulated PPP traffic.
L2TP does not provide encryption on its own, so it’s almost always paired with Internet Protocol Security (IPsec). IPsec provides encryption and authentication using algorithms like 256-bit Advanced Encryption Standard (AES) and protocols such as Internet Key Exchange (IKE). Unlike MPPE, these standards are considered secure against most modern threats.
In an L2TP/IPsec configuration, L2TP provides the tunnel through which data flows while the IPsec layer protects packets from inspection. This combination uses double encapsulation, meaning data is wrapped once by L2TP and again by IPsec. While this layering increases security, it introduces overhead, which can reduce speed.
If IPsec is configured incorrectly (using weak, pre‑shared keys or mismatched encryption settings, for example), the secure connections can fail or become vulnerable. Additionally, because L2TP uses fixed ports and IPsec may need NAT traversal support, connections can be blocked by firewalls or NAT devices unless they’re configured to allow passthrough.
Advantages of L2TP
Though it’s roughly the same age as PPTP, L2TP is still occasionally used, while the former is virtually extinct. This is due to a few key factors.
Improved security with IPsec
Unlike PPTP, L2TP is compatible with IPsec, a security standard still used today. IPsec can stand up to conventional attacks, but the standard implementation may be vulnerable to future attacks using quantum computers. More modern protocols have taken steps to deal with this looming threat. For example, Lightway was upgraded to integrate Module-Lattice-based Key Encapsulation Mechanism (ML-KEM) into a quantum-secure hybrid key-exchange method.
Stable and reliable tunneling
L2TP allows multiple tunnels and sessions to exist at the same time, providing added utility. Additionally, established tunnels typically remain stable. By separating the tunneling and encryption layers, L2TP paired with IPsec is good at maintaining connections even when network issues or latency fluctuations arise.
Broad compatibility across platforms
L2TP/IPsec support is built into most modern operating systems, including Windows, macOS, Linux, and mobile platforms. The protocol can tunnel different network types, and because it encapsulates PPP traffic, it can transport multiple network protocols and even simulate local area network (LAN) bridging across IP networks. This broad support makes L2TP/IPsec an extremely versatile option.
Disadvantages of L2TP
Despite continued use and clear advantages over PPTP, L2TP is still somewhat lacking when compared to certain newer protocols.

Slower speeds due to encryption overhead
While very fast on its own, applying encryption with IPsec can make L2TP significantly slower. Both L2TP and IPsec encapsulate all data separately, resulting in lower speeds compared to modern alternatives like WireGuard that avoid double encapsulation.
More complex to configure
Configuring L2TP/IPsec requires managing keys and security associations. This means setting up pre‑shared keys or certificates. Additionally, you need to make sure that both IPsec and L2TP are properly configured to avoid introducing vulnerabilities and connection failures.
May be blocked by some networks
L2TP/IPsec uses User Datagram Protocol (UDP) ports 1701, 500, and 4500, which can cause firewall and NAT issues. You may need to spend time configuring both to get the protocol to function properly. In contrast, most newer protocols seamlessly work with most firewalls and networks.
PPTP vs. L2TP: Side-by-side comparison
| Factor | PPTP | L2TP/IPsec |
| Security | Uses MS‑CHAP authentication and optional MPPE encryption (insecure) | Relies on IPsec for encryption (secure) |
| Speed | Very fast due to the lack of overhead and encryption | Slow when paired with IPsec due to encryption overhead |
| Compatibility | Built into many legacy operating systems | Widely supported across modern devices |
| Use‑case scenarios | Non‑sensitive tasks performed on legacy hardware (outdated and insecure) | General use (outdated but secure) |
| Setup complexity | Easy to configure; may require router passthrough or port forwarding to work behind NAT | More complex to set up; may need firewall rules for UDP ports 1701, 500, and 4500 |
When should you use PPTP or L2TP?
Outside of niche cases involving old hardware and tasks where security isn't a factor, there really isn't any reason to use PPTP today. When paired with IPsec, L2TP is acceptable in terms of security but still falls short in other areas. Both protocols were developed in the 1990s and have been superseded by newer, more robust alternatives.
WireGuard and Lightway surpass the pair in every notable area. They're faster, more secure, and offer greater overall stability. OpenVPN is another option. Though not as efficient as the other two, it’s still a much better choice than either PPTP or L2TP.
FAQ: Common questions about PPTP and L2TP
Is PPTP still safe to use?
The Point-to-Point Tunneling Protocol (PPTP) is insecure. Security researchers in the 1990s found fundamental flaws in Microsoft Challenge-Handshake Authentication Protocol version 2 (MS-CHAPv2) authentication and Microsoft Point-to-Point Encryption (MPPE) encryption. The certificate handshake can be cracked very easily, especially with modern technology. Additionally, the Generic Routing Encapsulation (GRE) data channel is usually blocked by firewalls.
Is L2TP better than PPTP?
On its own, the Layer 2 Tunneling Protocol (L2TP) provides no encryption, but when paired with Internet Protocol Security (IPsec), it offers encryption and strong authentication protocols. The double encapsulation process makes L2TP slower than the Point-to-Point Tunneling Protocol (PPTP). That said, PPTP is itself insecure, so we don’t recommend using it. For these reasons, most users will want to use a newer protocol that provides security without sacrificing speed.
Can L2TP be used without IPsec?
Yes, but it isn’t secure. The Layer 2 Tunneling Protocol (L2TP) only encapsulates data and does not encrypt or authenticate it. Without Internet Protocol Security (IPsec), anyone on the network could inspect or modify your traffic. When you pair L2TP with IPsec, the IPsec layer provides encryption and authentication to protect your network. In short, there are very few scenarios where you’d want to deploy L2TP on its own.
What is the fastest VPN protocol?
Protocols with minimal encryption overhead are typically the fastest. The Point-to-Point Tunneling Protocol (PPTP), WireGuard, and ExpressVPN’s Lightway protocol are all very fast. But despite this advantage, there’s very little reason to use PPTP as it is now considered insecure. Lightway and WireGuard, on the other hand, are both fast and secure.
Which protocol works best for streaming or gaming?
The Point-to-Point Tunneling Protocol (PPTP) is generally faster than the Layer 2 Tunneling Protocol with Internet Protocol Security (L2TP/IPsec), but outdated security protocols make it a risky choice, even for streaming and gaming. L2TP/IPsec is better than PPTP at protecting your privacy, but you’re still better off opting for a modern protocol like Lightway or WireGuard.
Is OpenVPN the same as PPTP or L2TP?
OpenVPN is markedly different. It uses Secure Sockets Layer (SSL) / Transport Layer Security (TLS) to establish encrypted tunnels and supports 256-bit Advanced Encryption Standard (AES) encryption. It’s newer than either the Point-to-Point Tunneling Protocol (PPTP) or the Layer 2 Tunneling Protocol (L2TP) and generally a much better option for securing your traffic. PPTP is now considered insecure. While L2TP is better in terms of security, there are very few reasons why you might choose it over OpenVPN.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN